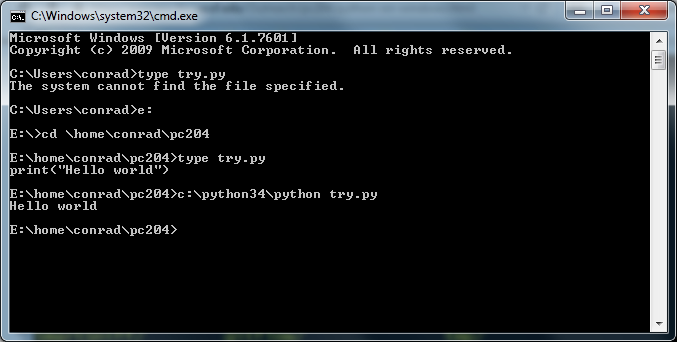
LogRecordobjects seize the msgand argsarguments of logging strategies and the exception and name stack data together with supply code information. They additionally seize the keys and values within the additional argument of the logging system as fields. Beyond logging levels, filtersprovide a finer means to filter log requests founded on the knowledge in a log record, e.g., ignore log requests issued in a selected class. Clients can add and take away filters to/from loggers utilizing Logger.addFilterand Logger.removeFiltermethods, respectively. Handlerskey maps to a dictionary of strings and dictionaries.
The strings function handler idsused to consult handlers within the configuration (e.g., including a handler to a logger) whilst the mapped dictionaries function handler configurations. The string worth of the classkey in a handler configuration names the category to instantiate to assemble a handler. The string worth of the levelkey specifies the logging degree of the instantiated handler.
The string worth of the formatterkey specifies the id of the formatter of the handler. Likewise, the listing of values of the filterskey specifies the ids of the filters of the handler. The remaining keys are exceeded as key-phrase arguments to the handler's constructor.
Essentia is an open-source C++ library for audio evaluation and audio-based music details retrieval. Essentia is cross-platform and designed with a specialise in optimization when it comes to robustness, computational speed, and low reminiscence usage, which makes it environment friendly for a lot of industrial applications. This coding sample avoids repeated invocations of the logging.getLogger()function to retrieve the identical module-level logger; hence, it helps get rid of redundant retrievals. However, such eliminations can cause misplaced log requests if retrievals will not be redundant. For example, suppose the logging library configuration in a long-running net service is up to date with this disabling_existing_loggersoption.
Since such an replace would disable cached loggers, not certainly one of several logging statements that use cached loggers would log any requests. While we will cure this example by updating cached references to loggers, an easier answer can be to make use of the logging.getLogger()function rather than caching references. MediaPipe Face Detection is an ultrafast face detection answer that comes with 6 landmarks and multi-face support.
It is predicated on BlazeFace, a light-weight and well-performing face detector tailor-made for cellular GPU inference. For extra details about BlazeFace, please see the Resources section. In the supported configuration scheme, we can't configure filters to filter past basic name-based filtering. For example, we can't create a filter that admits solely log requests created between 6 PM and 6 AM. We should program such filters in Python and add them to loggers and handlers by way of manufacturing unit functionsor the addFilter()method.
The handlers use their threshold logging degree and filters to filter log knowledge for processing. This further filtering permits context-specific manage over logging, e.g., a notifying handler have to solely course of log requests which might be important or from a flaky module. A consumer troubles a log requestby executing a logging statement. Often, such logging statements invoke a function/method within the logging APIby offering the log dataand the logging levelas arguments.
The logging degree specifies the significance of the log request. Log facts is usually a log message, which is a string, together with some additional datato be logged. A software-based keylogger is a pc program designed to file any enter from the keyboard.
Keyloggers are utilized in IT organizations to troubleshoot technical issues with desktops and commercial enterprise networks. Families and businesspeople use keyloggers legally to watch community utilization with no their users' direct knowledge. Microsoft publicly acknowledged that Windows 10 has a built-in keylogger in its ultimate variation "to develop typing and writing services".
However, malicious people can use keyloggers on public desktops to steal passwords or bank card information. The sensors have on-chip programmable acquire amplifiers and 10-bit A/D converters. The graphic black degree is both calibrated automatically, or might possibly be adjusted by with the addition of a consumer programmable offset. A four-wire serial peripheral interface with excessive degree programmability permits the consumer to examine out specified areas of interest.
Up to 32 areas could be programmed to realize even larger body rates. This flexibility allows PYTHON clients to determine the perfect gadget and the corresponding set-up for his or her wants and application. The second possibility is to initialize the logging library with a log report creating manufacturing unit perform by way of logging.setLogRecordFactory(). Loggerskey maps to a dictionary of strings that function logger namesand dictionaries that function logger configurations.
The string worth of the levelkey specifies the logging degree of the logger. The boolean worth of the propagatekey specifies the propagation setting of the logger. The record of values of the filterskey specifies the ids of the filters of the logger. Likewise, the record of values of the handlerskey specifies the ids of the handlers of the logger. Like loggers, handlers have a threshold logging level, which might be set by way of theHandler.setLevel method. They additionally assist filtersvia Handler.addFilterand Handler.removeFiltermethods.
Handlersprocess the filtered log files to both shop the log facts (e.g., write the log facts right into a file) or carry out different actions involving the log facts (e.g., ship an e mail with the log data). In some logging libraries, earlier than processing log records, a handler might once more filter the log files centered on the handler's logging degree and user-provided handler-specific filters. Also, when needed, handlers frequently depend upon user-provided formattersto format log files into strings, i.e., log entries. Based on how the logging library is configured , the logging library filters the log requests/records.
This filtering includes evaluating the requested logging degree to the edge logging degree and passing the log information by using user-provided filters. For this reason, the languages of selection for industrial and business robotics builders are people who supply worthwhile performance, normally on the price of readability and maintainability. The clear winner on this type stays good previous C, which is utilized in nearly all of these applications. In some cases, precise purposes use area of interest languages which might be particularly well-suited to the task. For example, I've heard that Ada is used lots for avionics. If you're enthusiastic about robotics and need to program industrial robotics system, I advocate mastering C.
This will permit you to work on superior robotics projects, and can make researching another language you're more seemingly to wish later a lot easier. The configuration schema for filters helps a sample to specify a manufacturing unit perform to create a filter. In addition, attributes and values could very well be added to customized filters by mapping the .key to a dictionary of attribute names and values. A stderrhandler that codecs log requests with INFO and better logging degree log by way of the simpleformatter and emits the ensuing log entry into the usual error stream. The streamkey is handed as key-phrase arguments to logging.StreamHandlerconstructor.
When concerned packages (e.g., apps, libraries) use the logging library, a stronger possibility is to externalize the configuration of the logging library. We check with this strategy to configuration as data-based approach. Msgand argsarguments within the above strategies are mixed to create log messages captured by log entries. All of the above strategies help the key-phrase argument exc_infoto add exception details to log entries and stack_infoand stacklevelto add name stack details to log entries. Also, they help the key-phrase argument extra, which is a dictionary, to cross values related to filters, handlers, and formatters. In this method, we'll use pynput python module to detecting any key press.
"pynput.keyboard" consists of courses for controlling and monitoring the keyboard. Stop from anywhere, or return False from a callback to give up the listener. This library permits you to regulate and monitor enter devices. This is without doubt considered one of many key motives that robotics programming is so difficult. We sometimes see movies of the newest analysis robotic within the lab, performing implausible feats of dexterity, navigation, or teamwork, and we're tempted to ask, "Why isn't this utilized within the true world?
" Well, subsequent time you see such a video, check out how highly-controlled the lab surroundings is. In most cases, these robots are solely capable of carry out these spectacular duties so lengthy because the environmental circumstances stay inside the slender confines of its inner model. Thus, one key to the growth of robotics is the event of extra complex, flexible, and strong models—and pronounced growth is topic to the bounds of the obtainable computational resources. Unlike handlers, the logging library solely can present a simple formatter that logs the requested logging level, the logger's name, and the log message. So, past elementary use cases, customers must create new formatters by creating logging.Formatter objects with the required format strings. The logging.Loggerobjects provide the first interface to the logging library.
These objects present the logging strategies to situation log requests together with the strategies to question and modify their state. From right here on out, we'll confer with Logger objects as loggers. After Listing 6-1 will get the pressed keys as an inventory of booleans, it enters a for loop that iterates by way of every value. You'll become aware of that the loop iterates over the pressed keys not instantly by calling enumerate, which is a built-in operate that returns a tuple of the index and the worth from the iterated list. If the iterated worth is True, then that key has been pressed, and we enter a small code block to display it on screen. This code block makes use of yet another operate within the keyboard module, pygame.key.name, which takes a key fixed and returns a string with an outline of the important thing (i.e., it turns K_SPACE into "space").
Just as deep studying has impacted just about each side of workstation vision, the identical is true for character recognition and handwriting recognition. Deep studying headquartered versions have managed to acquire unprecedented textual content recognition accuracy, far past conventional information extraction and machine studying photograph processing approaches. But once I change it to a Keyboard-sensor, it does not work. To preserve a hierarchy of loggers, when a buyer makes use of the logging library, the library creates a root loggerthat serves because the basis of the hierarchy of loggers.
The default threshold logging degree of the basis logger is logging.WARNING. The logging.Handlerobjects carry out the ultimate processing of log records, i.e., logging log requests. This remaining processing regularly interprets into storing the log record, e.g., writing it into system logsor files.
Each of those strategies is a shorthand to concern log requests with corresponding pre-defined logging ranges because the requested logging level. Each logger has a threshold logging degree that determines if a log request must be processed. A logger processes a log request if the numeric worth of the requested logging degree is bigger than or equal to the numeric worth of the logger's threshold logging level.
Clients can retrieve and alter the edge logging degree of a logger by approach of Logger.getEffectiveLevel()and Logger.setLevelmethods, respectively. One of Python's putting functions is its means to manage excessive visitors sites, with an emphasis on code readability. In this post, you'll discover examples of various outputs. In this article, we'll discover how can we detect if a selected secret is pressed by the consumer or not. Detecting a secret is vital for a coder, because the full execution of this system is simply depending on a single/pattern key press. Machine researching fashions are a strong solution to realize the info insights that give a boost to our world.
To study extra concerning the precise algorithms used with supervised and unsupervised learning, we encourage you to delve into the Learn Hub articles on these techniques. We additionally advocate trying out the weblog submit that goes a step further, with an in depth study deep gaining knowledge of and neural networks. Regression is a further style of supervised gaining knowledge of approach that makes use of an algorithm to know the connection between dependent and unbiased variables. Regression fashions are valuable for predicting numerical values headquartered on completely different knowledge points, resembling revenue sales projections for a given business. Some famous regression algorithms are linear regression, logistic regression and polynomial regression.
Supervised gaining knowledge of is a machine gaining knowledge of strategy that's outlined by its use of labeled datasets. These datasets are designed to coach or "supervise" algorithms into classifying facts or predicting outcomes accurately. Using labeled inputs and outputs, the mannequin can measure its accuracy and be taught over time.
Many anti-spyware purposes can detect some program primarily established keyloggers and quarantine, disable, or get rid of them. However, seeing that many keylogging packages are official items of program underneath some circumstances, anti-spyware generally neglects to label keylogging packages as spy ware or a virus. These purposes can detect software-based keyloggers primarily established on patterns in executable code, heuristics and keylogger behaviors . The logging library provides the keys of the extraargument as attributes to log records. However, if asctimeand messageoccur as keys within the extraargument, then the creation of log data will fail, and the corresponding log request is not going to be logged. If True, then solely logging degrees and propagate alternatives of loggers, handlers, and root loggers are processed, and all different bits of the configuration is ignored.
This secret is beneficial to change present logging configuration. When loggers with out handlers obtain log requests, the logging library directs such log requests to the final resort handler, which is a logging.StreamHandlerinstance structured on sys.stderr stream. This handler is accessible by way of the logging.lastResortattribute. When the manufacturing unit operate is used to create a logger, the operate units a logger's threshold logging degree to the edge logging degree of its dad or mum logger as decided by its name. The manufacturing unit operate logging.getLoggeris usually used to create loggers. By employing the manufacturing unit function, consumers can depend upon the library to administer loggers and to entry loggers by way of their names in preference to storing and passing references to loggers.
This Python tutorial assumes the reader has a superb grasp of programming in Python; specifically, ideas and constructs pertaining to normal programming and object-oriented programming. The facts and Python logging examples listed here are established on Python variation 3.8. The Python normal library can supply a logging module as an answer to log occasions from purposes and libraries.
Once the logger is configured, it turns into component to the Python interpreter course of that's operating the code. You can even configure Python logging subsystem utilizing an exterior configuration file. The specs for the logging configuration format are present within the Python commonplace library. Here, we're utilizing three techniques to detect keypress in Python read_key() , is_pressed() and on_press_key() .
The read_key() will learn which key a consumer has pressed on the keyboard, and if it's that key which you wanted, on this case, p , it can print the message You pressed p . One approach is to manage KEYDOWN events, that are issued when a key's pressed, and KEYUP events, that are issued when the secret is released. This is impressive for typing textual content in simple terms because we'll perpetually get keyboard occasions even when a key has been pressed and launched within the time in simple terms because the final frame. Events will even seize very speedy faucets of the important thing for hearth buttons. But once we use keyboard enter for movement, we in simple terms should know if the secret is pressed or not earlier than we draw the subsequent frame. In this case, we will use the pygame.key module extra directly.